Ethereum: 2FA or Multi-Factor Authentication for transactions
A multi-signature account as middleware between you and the dApps
Let's discuss security again and why you should move to a multi-signature account, even for your personal account. Many still consider multi-sigs as something for organizations to store assets, difficult to manage, or limited. None of this is true.
Externally owned accounts (EOAs)
These are the addresses and private keys we all use to communicate with the blockchain. There is no other way to do this, but the problem is - people directly communicate with the dApps - tokens, NFTs, stacking, DAO voting, and so on.
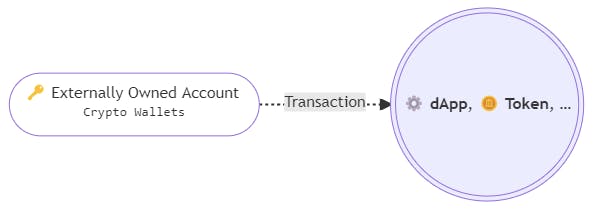
As the result, all assets are attached to that account, and it turns into a wallet, which holds all your funds. Though there are many ways you can try to secure your private 🔑KEY, all of them mainly go to checkpoints on how to secure your Operating System. Even hardware wallets can't protect your funds if your system is compromised and the malicious transactions are subscribed with the KEY. And I'm not talking about browser extensions, such as MetaMask, where in the worst case the attacker can get the seed phrase.
We had already the case when a person in our team had downloaded the malware from a phishing website, and his funds from the accounts, he used in MetaMask, were gone. He, a technically aware person, got a victim of the Oski Stealer.
But there is a much better way to secure the assets - to have multiple and rotatable 🔑KEYs with all funds on multi-sig.
Multi-signature accounts (Contracts)
A multi-signature account is a contract - living on-chain and being a proxy between your KEYs and the dApps.
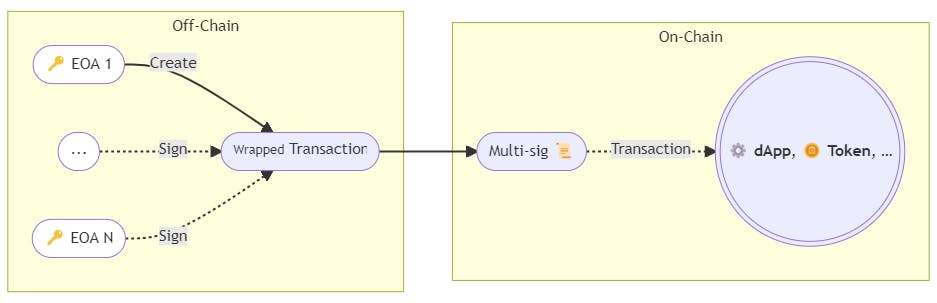
And as result, this is the wallet that holds all your assets. The multi-sig is like your personal guard, which can bypass only valid transactions, there are some rules you can specify - the number of required signatures, and spending limits.
🔑 Multiple Keys
For example, you can create a 2-of-2 scenario - you generate one private key on your machine, and the second on your mobile phone, and you set both addresses as owners into the multi-sig, after that, to create a transaction you need both signatures to add to it so that the multi-sig passes the transaction through. And this is the 2FA for transactions:
- Create a transaction on your machine with the first signature.
- Review and sign the transaction on your mobile.
You still have to protect your devices, so that the KEYs stay safe, but this drastically increases the security. This mitigates even phishing attacks, as you 👀 double-check the transactions.
🔃 Rotatable
While your assets are owned by your multi-sig account and your EOAs are just the KEYs to that account, you can create new KEYs and replace them in the multi-sig at any time. So if you have any doubts you could be compromised - replace the affected address. Or you can do this on a regular basis - once half a year - change the KEYs.
✳️ A noncustodial solution, and no vendor locks
I saw some beliefs, that Gnosis Safe Multisig is a custodial wallet, for those people — see the section about Gnosis Safe below.
🔥 Edge cases and the caveats
There are some situations when you can't use multi-sigs, but all of them are just limited by the dApp implementations.
Message signing. EOAs can sign messages with their associated private keys, but currently, contracts cant. There is a solution for this — eip-1271, but it should be implemented and supported by the dApp
tx.origin. Not so common as the previous one, but some contracts explicitly checkmsg.sender == tx.origin, which means they restrict forwarded transactions and require the caller to be an EOA, not the contract. I've met this only once by Alpaca Finance.slightly higher ⛽GAS consumption
No easy-to-use solution yet, like the MetaMask browser extension. It is possible to connect via WalletConnect, though it is also limited to allowed dApps.
Gnosis Safe
I use Gnosis Safe multi-signature contracts, as the most established solutions in this area. As I've said previously, this is not a custodial multi-sig, to understand this, you should know how it works. It consists of 2 parts:
Multisig Contract. Once you've created this on-chain, this contract belongs to you. You are the owner, and only you have access to it. Gnosis shares its implementation with you so that you could create the contract.
Off-chain Transport. Gnosis web app and Gnosis Safe mobile applications are just the clients for your multi-sig contract, but you can create multi-sig transactions and collect signatures without Gnosis Safe infrastructure.
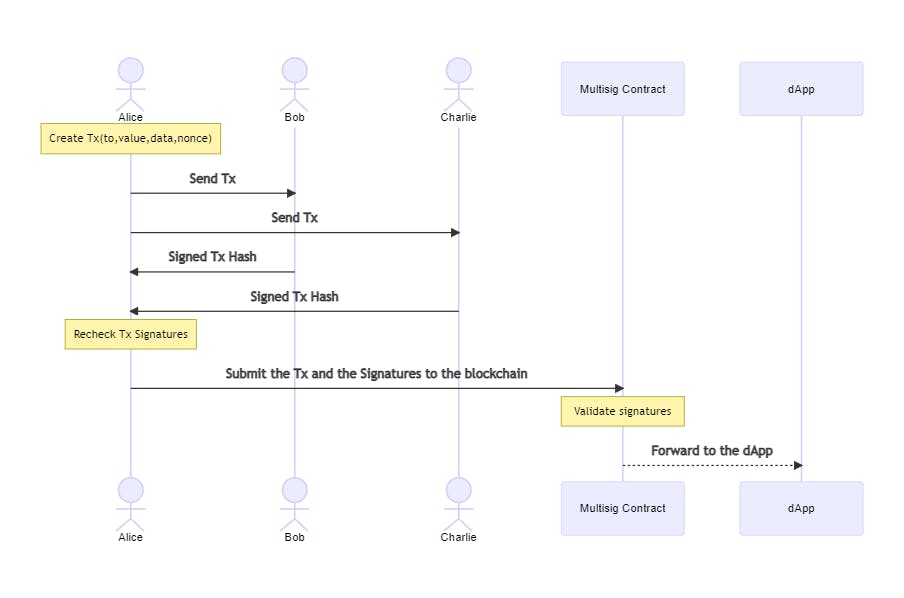
As an example, you can send your desired transaction data to participants via e-mail as a JSON file and collect the signatures back. The transport doesn't need to be secure, a man-in-the-middle can only see what transaction you want to send, but can't manipulate it. Also, no private keys are disclosed.
0xWeb
Here I will show, how I use the 2FA for my transactions. 0xWeb is a CLI wallet with the ability to install validated contracts from Etherscan and other EVM blockchain explorers — it generates TypeScript client classes that can be used via CLI or API. But to keep it simple, for an example, I will create a simple transfer transaction.
Create or Add EOA/Safe accounts
- 📱Create a "FooMobile" account in Gnosis Safe App. Go to "Settings 🠖 Owner Keys 🠖 ADD 🠖 Create new owner Key"
- 🖥️ Create a "FooDesktop" account in 0xWeb CLI.
$ 0xweb accounts new --name FooDesktop --pin <pin> - 🖥️ Finally create the multi-sig. We add to members the address of the account we've created in GnosisSafe
$ 0xweb safe new --name safe/foo --owner FooDesktop --members 0x<...> --chain eth - 📱Add the Multisigs Address to Gnosis Safe App Go to "Menu🠖 Add Safe 🠖 Select Chain 🠖 Enter the address"
You see, I've created the keys on different devices, with different vendors, and none of the will store both private keys.
Perform arbitrary transactions, for example, transfers
Assume we sent some ETH to the safe, and later want to transfer some from the safe to another address.
$ 0xweb transfer 0.04 ETH --from safe/foo --to 0x<...> --pin <pin> --chain eth
After I run this command, I receive the push notification with the Tx Proposal on my mobile, I review and confirm the transaction, something like this:
0xweb tool waits until the Gnosis API Service returns the required signature and submits the Tx to the blockchain.
Backend
Not only for personal use but also for backends we use the multi-sig approach. There is an additional validator instance. We store all assets on multi-sigs, and for example, when a user wants to withdraw assets, in our main backend we validate the intent, create a tx proposal, and send these to the validator backend, that one validates the intent with the tx once again, and sends its confirmation back to the main server, which sends the Tx to the blockchain.
Summary
I'm still wondering, why the EOA wallets are still popular to store funds on when MultiSigs are much more secure. I hope browser wallets, like MetaMask, will add the MultiSig support, so we can connect to dApps with the multi-sig account, and before the transaction is submitted, we have to confirm it with our mobile app.
Stay safe. 🔒

